Recently, Florian Adamsky presented a paper at a USENIX Workshop on Offensive Technologies. The paper reported on a study his team conducted on the possibility of exploiting BitTorrent protocols for Distributed Reflective Denial of Service Attacks (DRDoS). The risk being that an attacker could exploit a user unknowingly and have them direct traffic to a victim at such volume as to take them offline. Their net conclusion was that there were some vulnerabilities.
Thankfully, no such attack has yet been observed in the wild and Florian responsibly contacted us to share his findings. This gave our engineering team the opportunity to mitigate the possibility of such an attack. Today, a post from Francisco De La Cruz describes how such an attack would work and the steps we have taken to reduce its potency.
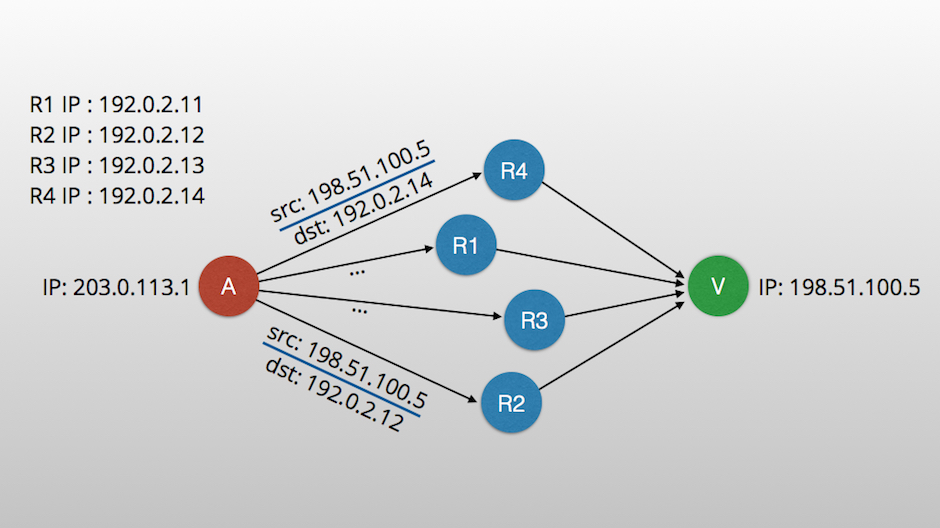
In short, the efficacy of this type of attack is commonly measured by how much traffic an attacker can direct toward the victim, known as the Bandwidth Amplification Factor (BAF). A high BAF indicates an efficient attack while low BAF indicates a low efficiency or high-effort attack.
By enforcing the requirement for a potential target reflector to receive a unique acknowledgement number when receiving traffic, the BAF ratio can be reduced. It would be fairly difficult for an attacker to guess the acknowledgement number for a sufficiently large number of targets. This means that any packets falling outside of an allowed window will be dropped by a reflector and will never make it to a victim.
The details can be found in Francisco’s post on our Engineering Blog. We’ll continue to update as needed.
An important point regarding Sync: Even before the recent updates to Sync, the severity of the vulnerability was reduced by a few factors. First, the attacker would have to know the Sync user they are trying to exploit to get their “Secret” – or the Sync user would have to have exposed that “Secret” publicly in some way. In addition, Sync, by design, limits the amount of peers in a share making the attack surface much smaller. It would not serve as an effective source to mount large scale attacks.
This is a serious issue and as with all security issues, we take it very seriously. We thank Florian for his work and will continue to both improve the security of these protocols and share information on these updates through our blog channels and forums.